My blog posts represent a white board of sorts for some of my notes, hopefully coherent, that will serve as a taking-off spot for topics I plan to include in my next book focused on the insurance industry and cyber. The book is currently in the planning, framing, and research stages.
In this blog post I discuss: cyber insurance advisors, the cyber age, the cyber age’s impact on the insurance industry, and insurance commerce in the cyber age, including customer interaction paths, and a high-level systems perspective.
As context for this blog (and actually, every blog, report, and book I write), please keep in mind that I believe that no line of insurance is a commodity. The sales and service activities of insurance commerce – whether commercial lines or personal lines – should involve an insurance professional offering consultative advice to the client.
Cyber insurance advisors
In the cyber insurance market, the professional providing the advice to prospective commercial clients could be an insurance agent or broker (or MGA or MGU).
However, increasingly the insurance producer will be joined from one or more professionals from some combination of the following:
- one or more cyber protection services firms including firms (in a continually expanding, fragmenting, and integrating) frothy cyber advisory market area providing:
- cyber audits
- cyber security
- cyber resilience
- cyber modeling
- cyber incident response
- inside-out real-time monitoring
- outside-in real-time monitoring
- risk quantification and management
- managed service providers (MSPs)
- managed detection and response
- security operations center (SOC) service
- other cyber protection and/or analytical services and/or advisory services
- law firm with cyber law experience and preferably knowledge of cyber insurance policies
- external risk management services firm.
I find the expanding number of cyber insurance “advisory categories” interesting and logical.
Why?
Interesting: Because only insurance producers (agents, brokers, MGAs, MGUs) are regulated, licensed, and certified by insurance regulators to legally sell and service insurance. I imagine there may be one or more licensed (to sell and service cyber insurance) insurance producers working for firms in the 2nd and/or 3rd category. I’d be curious to determine if that was true.
Logical: Because cyber risks exist and emerge from some combination of digital artifacts, digital content of physical artifacts, and physical artifacts. To say that cyber risks are significantly different than the risks generated by the various combinations of physical artifacts, nature, and/or human activities would be a gross understatement. No, Virgina, cyber risks are nothing like what you’ve seen before in the hundreds of years of the insurance industry’s existence.
Five implications from the expanding universe of cyber insurance advisors:
- Partnerships: There will be more partnerships between members of the 2nd and/or 3rd group with insurance brokers (and/or with insurance carriers offering cyber insurance).
- Acquisitions: More insurers offering cyberinsurance will acquire firms in the 2nd group (such as Zurich Holding Company of America’s August 14, 2023 acquisition of Spear Tip.
- Stepping over the regulatory line: There will be members of the 2nd group and/or 3rd group “stepping over the insurance regulatory sales and service lines” either purposely or mistakenly by offering cyber insurance advice to clients. Of course, the key issue is when “advice” becomes action that only insurance brokers can legally offer.
- Holistic view of all risks required: Commercial clients – regardless of the size of their company – have more than cyber risks to be covered. They need an insurance producer to consider what their entire comprehensive insurance portfolio should be to cover all of their company needs. Leaning on members from Group 2 or 3 would be detrimental to the company’s risk coverage health.
- Diverse team of IT and Telco experience and skills required: Insurance producers can’t possibly understand the current and potential forms of cyber attack spaces and cyber attacks that will emerge during the months and years ahead as interconnections and interdependencies continue to form between and among digital artifacts, digital content of physical artifacts, and artifacts. (Neither can the commercial clients or any of their cyber protection firm advisors. Cyber risks present a situation where a diverse portfolio of IT, Telco, and modeling skills and experience is needed to enable the client to become and remain cyber resilient and cyber secure.)
[I’m looking forward to feedback from LinkedIn members about whether I’m wrong in my comments above; what partnerships they’re seeing or are involved with concerning advising clients about cyber security; and where they see the “advisory” players portfolio going.]
The Cyber Age
What do I mean by the Cyber Age?
I agree an argument can be made that the Cyber Age began when the first programmable, electronic, general purpose digital computer was turned on in 1945 (ENIAC; Electronic Numerical Integrator and Computer – Source: Wikipedia, https://en.wikipedia.org/wiki/ENIAC). Personally, I think of that as the beginning of the Computer Age.
However, I submit that the Cyber Age was born with the confluence of digitization, mobility, the web (actually, the Internet), and the cloud. As more and more technologies and their concomitant applications emerge from each of these four influences and also with the deployment of two or more of these four influences, the Cyber Age strengthens its reach through society and branches out into hyper dimensional spaces.
For me, the Cyber Age is best described as the never-ending, continually forming plethora of interconnections and interdependencies among and between digital artifacts, digital content of physical artifacts (e.g. IoT), and physical artifacts generating yet-to-form cyber attack spaces and yet-to-emerge cyber attacks.
I suggest that professionals involved in any aspect of cyber (whether from the cyber insurance industry, a member of a cyber protection services firm, a cyber risk professional such as a CISO, a risk manage or CFO or other company executive responsible for cyber security / resilience, or an industry or government entity writing cyber regulations) should realize that the current state of the Cyber Age in 2023 – including its associated portfolio of cyber risks, cyber attack spaces, and cyber attacks – is as far from being ‘mature’ as the distance from Earth to the most distant galaxy known to scientists.
Five attributes of the Cyber Age
The Cyber Age brings with it four attributes that distinguishes it from previous eras, specifically because physical artifacts (augmented by some combination of geography, people, and nature) were the central element of all of the previous era’s life, work, communications, entertainment, socialization, and, of course, risks:
- Immediacy / Real-Time
- Scale
- Reach
- Hyper-dimensions
All or most of these attributes are present as cyber attack spaces are formed and yet-to-emerge cyber attacks actually emerge. These four attributes are part-and-parcel of a cyber attacker’s toolkit (which taken together generate an additional, and critically important, fifth tool for them: stealth) and will continue to provide (cyber) predators an advantage over (cyber) prey. [Stealth: The Fifth Tool – good title for a future cyber blog post.]
Cyber Age’s impact on the insurance industry
As an insurance industry analyst, I always told clients that technologies and their associated applications impact the insurance industry in two significant ways, they: 1) provide capabilities for insurers to become more efficient and/or more effective supporting operational and decision-support business objectives; and 2) change the risk landscape.
The Cyber Age (specifically the confluence of the four influences of digitization, mobility, the web, and cloud technologies and concomitant applications that together have formed and are continually expanding it) are impacting the insurance industry not only in two significant ways (operational, communication and collaboration, and decision-support; changing the risk landscape) but also a third one (monitoring and cyber securing each of the insurance commerce processes):
- Operational, communication and collaboration, and decision-support: Insurance carriers – whether they offer cyber insurance or not – have to identify and secure cyber attack operational, communication and collaboration, and decision-support process (and underlaying activities of the processes), spaces:
- Within their own company;
- Within, across, among, and between the companies and people participating in the ecosystems the carriers use (with the understanding that the companies and people change through time);
- Within, across, among, and between the companies and people participating in the ecosystems’ ecosystems.
- Changing the risk landscape: Insurance carriers offering cyber insurance (whether to commercial lines or personal lines clients) should be able to identify (with some degree of specificity) the current and model the potential future cyber attack spaces and both the associated cyber resilience and cyber security capabilities facing:
- Their prospective clients;
- Their prospective clients’ ecosystems;
- The companies and people participating in the prospective clients’ ecosystems’ ecosystems.
- Monitoring and cyber securing insurance commerce processes: The insurance industry (cyber) securing their own (transactional and relational) commerce processes and activities that are vulnerable to cyber attacks whether the processes are used to:
- go-to-market;
- get-and-keep clients;
- get-and-support brokers (and other insurance producers as well as other participants in the insurance commerce ecosystem);
- support any of the various operational, financial, decision-support, strategic, and tactical initiatives.
My statement of vulnerability in #3 assumes that at least one activity of one process is web-accessible regardless of whether the web-accessibility is from the insurance carrier, any person or company in the carrier’s ecosystem, any person or company participating in the carrier’s ecosystem’s ecosystem, any prospective client of the carrier, any client of the carrier, or any prospective client or client of the carrier’s ecosystem or carrier’s ecosystems’ ecosystem.
Note: My definition of “ecosystem” for this post is any third-party company working for an insurance company that provides services as a channel, producer, supplier, reinsurance company, partner, legal counsel, claim adjudicator, bank, digital marketplace, or subcontractor of any of a variety of other services the insurance carrier contracts for at a point-in-time.
Insurance commerce in the Cyber Age
A communication and collaboration consideration of commerce
Commerce, whether insurance commerce or any other type of commerce, is essentially a mix of and/or interconnected communication and collaboration information flows to support clients, prospects, sales and distribution channel participants, and ecosystem participants.
These information flows are supported by, flow into, and flow out of:
- Legacy operational / transactional / interactional business systems (found in abundance in insurance carrier’s business system processes);
- VRUs or chatbots used:
- within functional departments;
- between clients and the insurance car carrier;
- between clients and broker firm, broker, claim adjudicator;
- Participating firms in a company’s ecosystems;
- Communication and collaboration applications among and between clients with professionals in the insurance carrier, broker firm, claim adjudicator firm, and other participants in the insurance commerce ecosystem.
The “information” could be text, documents, images (pictures or video), sound, or numeric or any combination of all of these possibilities
Looked at another way, these commerce information flows:
- Are initiated and maintained between and among various participants, some of which are software solutions (and not human);
- Encompass different types of structured and unstructured data;
- Could be real-time in nature or significantly slower (e.g. no response to a client query for a number of days);
- Could be either synchronous or asynchronous or a mixture;
- Move through IT and/or Telco solutions (created and deployed in-house; using packaged 3rd party solutions customized internally, or using packaged 3rd party solutions maintained only by 3rd parties);
- Could be stored on-premises, the public cloud, or a hybrid private / public cloud.
Customer interaction paths
Commerce is conducted along one or more customer interaction paths. (See visual.)
I believe that there has been an evolution of the nature of customer interaction paths that have encompassed four phases (see the visual for the different types of commerce capabilities in each phase):
- Geographically-bound commerce
- Online, digitally-bound commerce
- Online mobile commerce
- Online, immersive mobile commerce
We all know that a later phase does not replace previous phases. Each phase and each new capability in the phase offers more choice to clients but also “offers” more expense (and training) to insurers, brokers, and other involved commerce participants.
Clients as well as carriers, brokers, claim adjudicators, and other participants in the various insurance commerce processes use most of the capabilities in the first three phases. I’m curious how many insurance commerce participants – specifically insurers, brokers, claim adjudicators) are using the capabilities in Phase 4 other than virtual assistants (between the company and the client). [Yes, I’m also wondering how many are using virtual assistants …]
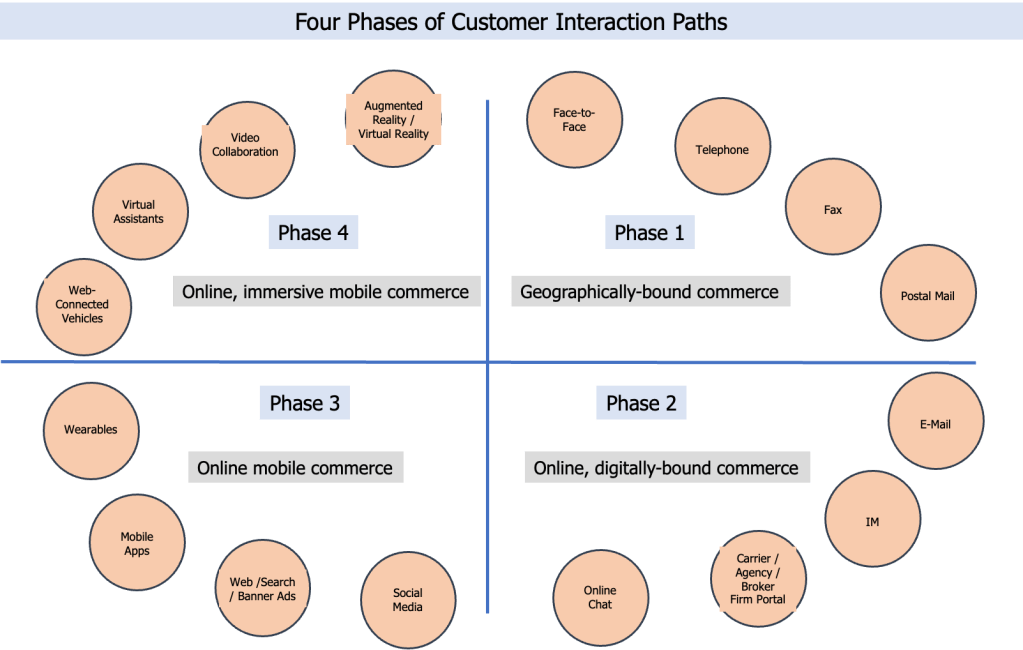
Of course, once commerce “graduated” from Phase 1, each of the new(er) phases has brought with it – and generated – cyber attack spaces and potential cyber attacks. Leaving geographically-bound commerce is the “gift that keeps on giving” to cyber attackers.
Insurance commerce, and commerce more generally, has become “ground zero” for cyber attacks whether to satisfy cyber attackers desire for financial rewards or to satisfy their desire for corruption, disruption, or destruction of the various commerce processes.

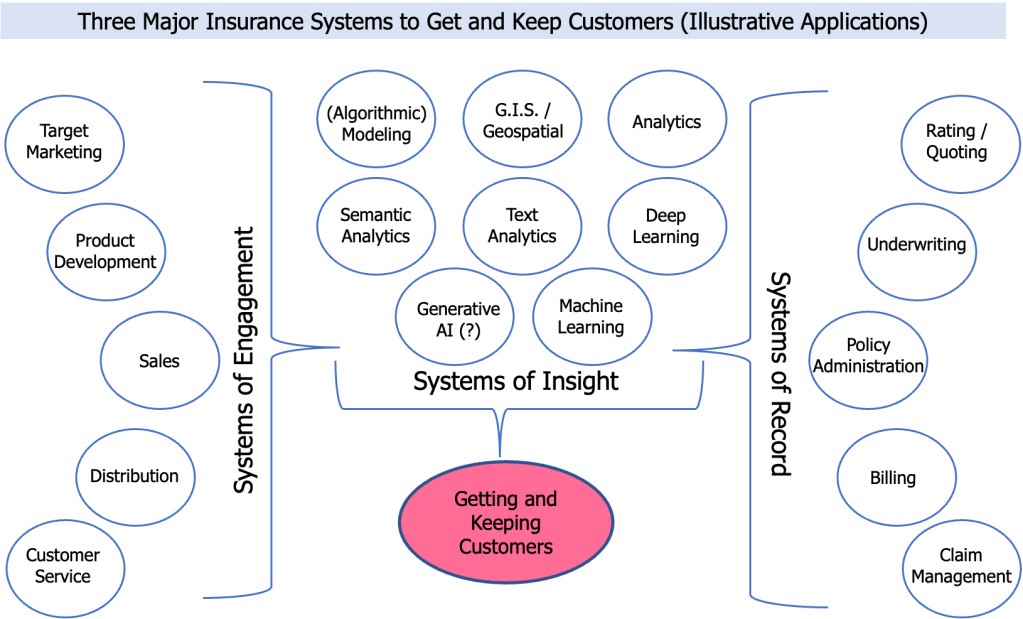
Insurance Commerce – Illustrative High-Level Systems Perspective
Delving into insurance commerce just a tad deeper, we immediately come to major insurance systems that enable the various transactions and interactions that are the essence of communications and collaboration to get-and-keep customers: Systems of Record, Systems of Engagement, and Systems of Insight. (See visual of three major insurance systems.)
These systems taken individually or collectively, enable (or provide the Systems of Insight support for decision-making to improve the effectiveness or efficiency about these and other actions to get-and-keep customers) as only a few examples:
- Making customers aware of new products
- Customer policy application and carrier underwriting
- Billing and premium collection
- Customer notification of a loss
- Broker commission payment
[Note: The various system components are illustrative and are not a complete list. Certainly, the examples I show within Systems of Insight comprise only a selection. Moreover, to those who cry out “where is is ChatGPT?” my answer is whatever applications of ChatGPT exist can be (will be?) found within one or more of the system components (e.g. Target Marketing). ChatGPT is a technology that can (might?) enable one or more of the system components. It is NOT a business function onto itself.]
TBD
Likelihood of Cyber Attacks Being Successful
Now, let’s consider the likelihood of cyber attacks being successful against insurer’s various systems regarding whether the system was built in-house and where the system is deployed.
In the following visual, I assume systems which:
- insurers build, deploy, and maintain in-house (e.g. on-premises) are more likely to be successfully cyber attacked than systems that insurers purchase from technology firms regardless of whether the system is deployed on-or-off premises;
- insurers develop and deploy on-or-off-premises have the same likelihood of being successfully cyber attacked;
- technology firms build, deploy, and maintain off-premises have lower likelihood of being successfully cyber attacked than deploying the system on-premises of the insurance company;
- are created, deployed, and maintained by technology firms off-premises in single-tenancy (rather than multi-tenancy) are less likely to be successfully cyber attacked than if the technology firms deployed them as multi-tenancy. (Not shown in visual.)
My assumptions are based on technology firms operating on the core principal that their cloud-based systems have to be more secure than the gold in Fort Knox. I fully realize that my assumption could very well be wrong. I haven’t been briefed by Guidewire, DXC, Insurity, OneShield, Applied Systems, Vertafore, Salesforce, or other technology firms providing insurers with packaged solutions (whether deployed on-premises or off-premises).

More Needed
Obviously, there are other details needed about the topics I have discussed in this post and, as importantly, on related insurance commerce issues from a cyber perspective.
Some of that will show up in future blog posts. Most of it will be in my next book.