Game of Thrones, Season 7, Episode 3 – After the Lannister army had marched on Highgarden, Jamie Lannister went to visit Lady Olenna in her room. And before she drank the poison he gave to her, she told him: “Whatever I imagined necessary for the safety of House Tyrell, I did,” says Olenna. “But your sister (Cersei Lannister) has done things I wasn’t capable of imagining. That was my prize mistake. A failure of imagination.” (Image Source: Bing.com)
I submit that a “failure of imagination” will be the death knell of insurers striving to achieve profitable success during the time period that insurers continue to offer cyber insurance. (Profitable success = combined ratios under 100%)
The world of Game of Thrones described – briefly
The HBO series “Game of Thrones” was a world-wide phenom premiering in the US on April 17, 2011 and finishing May 19, 2019. The world of Game of Thrones was a world replete with dragons, witches, sorcerers, seven kingdoms striving to find the best way to capture the throne, a sociopathic young king (whose cruelty knew no bounds), his mother, an extremely vicious person willing to do anything for her family to remain in power on the throne, Greek Fire, a woman with expanding power (dragons, armies, and ships) aggressively making the requisite moves to capture the throne her family lost, and initially a myth but soon realized as a reality, an army of the walking dead intent on killing all of the the living.
Essentially, the world of Game of Thrones was a world of murder, magic, and fear. The risk of staying alive was ever-present (and low odds). The Game of Thrones coin of the realm was power and it was absolutely necessary to beat the odds to living longer and/or win the Game of Thrones.
The cyber world described – not so briefly but not so detailed either
The Cyber World just didn’t emerge out of whole cloth. The Cyber World has been, and continues to be, created and woven together by five technology forces (including their changing mix of associated applications): digitalization technologies, mobility technologies, cloud technologies, Internet technologies, and AI technologies. (See visual).
This infrastructure, enabled by the fusion of information technology and telecommunications, provides society with the ability to continually interconnect people, corporations, digital artifacts, and sensor-embedded physical artifacts (and sensor-embedded animals) together.
These five pillars of the cyber world (digitization, mobility, cloud, Internet, and AI), individually and more importantly taken together, are riddled with current and yet-to-emerge cyber risks.
Moreover, the intersection of the pillars, inclusive of new and emerging applications of the five macro technologies, provides the digital materials for new and mostly unimaginable cyber risks to emerge that will cause societal havoc for people and companies in the forms of financial loss / theft and fraud as well as corruption, disruption, and destruction of intangible assets and probably tangible assets (whether belonging to people, companies, or governments).

[Unashamedly putting in a marketing plug, the cyber world is what I called “The 5th Technology Era” in my first book: “From Stone Tablets to Satellites: The Continual Intimate but Awkward Relationship Between the Insurance Industry and Technology”. You can find my book on Amazon in one of four formats: Kindle, paperback, hard cover, and Audible.]
Note: I may not be remembering correctly, but I thought I heard Jen Easterly, Director of the Cybersecurity and Infrastructure Security Agency (CISA) use those three terms (corruption, disruption, and destruction) referring to cyber attacks in a videos that one of my LinkedIn members posted. I apologize if it was some other person who brought up those terms. The three-word phrase certainly resonated with me as a succinct manner to identify three various types of macro damage from cyberattacks.
Consideration of some of the elements of the cyber world
The world of cyber is a world replete with an increasing number of:
- interconnections and interdependencies among and between digital artifacts, digital content of physical artifacts, and physical artifacts;
- never-ending newly-forming cyber attack spatial topographies;
- new and/or more aggressive cyber-attackers yet-to-emerge;
- never-ending and yet-to-emerge cyber attacks;
- IoT devices (The latest IoT Analytics “State of IoT—Spring 2023” report shows that the number of global IoT connections grew by 18% in 2022 to 14.3 billion active IoT endpoints. In 2023, IoT Analytics expects the global number of connected IoT devices to grow another 16%, to 16.7 billion active endpoints. Source: https://iot-analytics.com/number-connected-iot-devices/ );
- cybersecurity regulations from governments and industry associations around the world;
- short-sighted cybersecurity regulations focused on punishment of Boards of Directors or CISOs or both;
- Incident response firms, inclusive of firms offering (near) real-time cybersecurity protection (inside-out and outside-in?);
- cyber auditing firms;
- law firms assisting clients prepare for insurer’s cyber applications as well as provide legal assistance for cyber claims;
- Insurance broker firms who unfortunately can only see the potential rapid cyberinsurance premium growth (and not the downside of unprofitable business);
- Insurance carriers who unfortunately can only see the potential rapid cyberinsurance premium growth (and not the downside of unprofitable business);
- still-to-come instances of systemic and possibly catastrophic cyber risks (not being insurable by any one (re)insurer or even a plethora of (re)insurers);
- still-to-come instances of aggregate cyber and other P&C risks (not being insurable by any one (re)insurer or even a plethora of (re)insurers).
Essentially, the world of cyber is an expanding environment of wireless connectivity linking together an increasing number of digital assets, digital content of physical artifacts, and physical artifacts across and within each one of society’s realms (e.g. terrestrial, spatial (and geospatial inclusive of orbiting satellites), oceans / rivers / waterways).
The ability to imagine, identify, and model the losses generated from emergent cyber risks decreases – perhaps exponentially – as the expansion of wireless connectivity continues unbounded.
The coin of the realm in the cyber world is intangible assets.
Cyber risks – not the same as legacy risks
I repeat: the coin of the realm in the cyber world is intangible assets.
Intangible assets include digital artifacts, the digital content of physical artifacts, intellectual property, knowledge, and goodwill (at a minimum).
Imagining, measuring potential maximum cyber losses, and deciding whether to insure (which) cyber risks attendant to intangible assets or not (and at what coverage limits and with what terms, conditions, and restrictions) is the greatest challenge any cyber insurer faces (even if the coverage is actually “silent cyber”). (I think that corporate risk managers and CISOs also should, and probably do, travel this same path to decide what their firm requires for cybersecurity [on an ongoing basis] and whether – and how – to self-insure the cyber risks and associated losses they have imagined and measured.)
Concerning legacy risks: Throughout the extremely long history of the insurance industry, risks have been the result of some combination of people, nature, and physical artifacts. The world of these risks, while extremely large, is identifiable and measurable.
However, in the still forming cyber world, risks (e.g. existing, emerging, and still-to-emerge cyber risks) are and will primarily be the result of some combination of the interconnections and interdependencies of people, nature, intangible assets [digital artifacts, digital content of physical artifacts (yes, IoT and connected devices)], and tangible assets [physical artifacts].
This world of cyber risks is a continually expanding Nth dimensional world (e.g. spreading like an alien spore expanding in all dimensions in space from some science fiction horror movie) and the risks will mostly be neither identifiable (until the attacks have occurred) or measurable beforehand.
The nature of cyber risks include, but are certainly not limited to:
- Systemic Risks / Catastrophic Risks (If a Salesforce cloud is hacked corrupting the data – and/or holding hostage the data – of every client company using that cloud even if the company is using single tenancy in the Salesforce cloud, isn’t that an example of a systemic risk? Same question for insurance companies using a Guidewire cloud solution? Same question for insurance brokers using an Applied Systems cloud solution?);
- Business Technology Application Risks (which could also be systemic risks but I include ‘point’ or bundled solution technology application risks such as ERM, CRM, or billing applications);
- Productivity Software Solutions Risks (including hacks of Microsoft Office Subscriptions to take data hostage);
- Personal Software Solutions Risks (including hacks of cloud-based consumer note-taking software or journaling software);
- Internet Asset Risks (including hacks of domain name servers to cause disruption and corruption of all ‘downstream’ intellectual property using the DNS);
- Digital / Physical Risks (e.g. IoT) (cyber hacker taking control of an EV – or a Tesla CyberTruck – during rush hour traffic in a major city causing multiple crashes, injuries, and deaths);
- Frontier Technology Risks (e.g. Deepfakes, Generative AI, Immersion applications such as AR / VR / Hybrid Reality) (cyber hackers using Deepfakes to gain control of bank accounts … or working with other cyber hackers to use Deepfakes to file claim losses for supposedly damaged cars);
- Human Risks (humans will continue to cause cyber losses by, at a minimum, falling for phishing attacks, keeping their passwords [and pass-phrases] in plain view, clicking on links or email requests that they shouldn’t, and mistaking Deepfakes for the reality;
- Combination Risks (of two or more of the above risks, possibly inclusive of risks not delineated above).
Imagining emerging or new risks in the cyber world
So, into this brave cyber world we go because we have no choice in the matter (because it is all around us and it is redefining – and will continue to redefine – how society functions). And in this never-ceasing to expand cyber world, being able to identify, and more importantly estimate the probable maximum loss of each risk, is a foundational activity for every company and, of course, for every (re)insurer or E&S insurer (or capital market player). (I wrote this blog post in 2023. I will discuss ILS cyber cat bonds in my book.)
Primary insurers, E&S insurers, reinsurers – and capital market players – must decide whether to accept any specific cyber risk, and if deciding yes, then strive to successfully underwrite the risk to generate profit, however each type of insurer (and capital market player) defines “profit” for their company.
For me, there is a key hypothesis at play driving the need to accurately estimate maximum loss (which I believe is mandated for insurers to accept any risk):
Hypothesis: If an emerging or new cyber risk can not be imagined,
- financial losses from an emerging risk (or yet-to-emerge risk) can not be modeled;
- without a model, insurers can not estimate their maximum probable losses from the coverages they underwrite and sell for that emerging risk;
- insurers, at least primary insurers, are gambling with their financial capacity and simultaneously demonstrating very poor fiduciary responsibility.
But how to imagine emerging or new cyber risks? I believe the answer to that question is to imagine emerging cyber risks – or cyber attacks – as if you were a predator instead of the reality of your company being prey (always will be a victim, even if your company has already been a victim).
Playing in the voids
(Re)insurers (and risk managers and CISOs) will need to answer these questions to begin imagining where new or emerging cyber risks will emerge: Where will the new cyber attack spaces form? Where will the new cyber attacks hit?
For cyber attackers, it is an extremely rich – and continually expanding – target space. And I do mean ‘space’ – an ever-expanding multidimensional space because:
- The interconnections of systems is true within companies (regardless of size), true among and between industry ecosystems, and true throughout supply and logistic chains for various companies, markets, and industries.
- The interconnections of systems holds true for private homes, for farms and ranchers, for hospitals / medical offices, and for sports and entertainment venues.
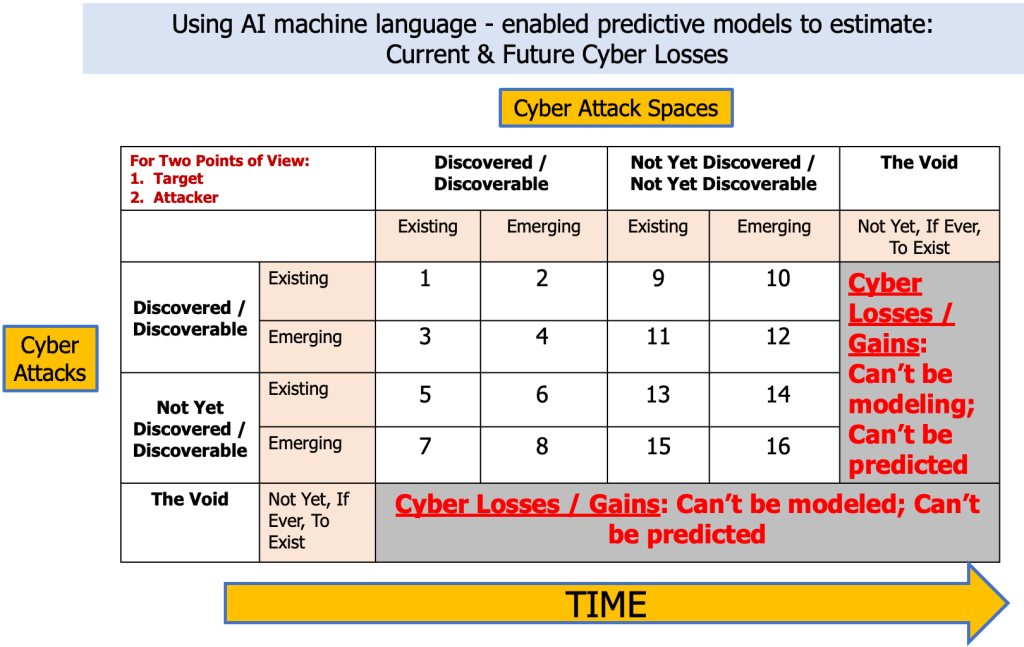
Some of the answers to the questions can be found by delving into the “Discoverable” components of the “Existing” and “Emerging” Cyber Attack Spaces and Cyber Attacks. They are logical extensions (perhaps with some non-linear mental breakthroughs) of what has already been “Discovered”. (See visual.)
But, I believe that it is by “playing in the voids” that imagination worthy of Game of Throne’s Cersei Lannister will identify possible forms of yet-to-emerge cyber attack spaces and cyber attacks.
(As you see, I labeled the chart with “Using AI machine language-enabled predictive models to estimate: …” Perhaps Generative AI might be of assistance?)
To be honest, the issue that I continually struggle to describe in a manner that it resonates with insurance firms, is that cyber risks are not the same as legacy risks and are inherently uninsurable. I have yet to snap them out of the “Yea, wow, new coverage … there is a lot of money to make because every firm of every size, wherever they are on the planet, needs cyber coverage”. At least from what I can see in my LinkedIn threads and articles in the insurance media.
One fear I have are the insurance professionals who have been involved with cyber since the beginning (sometime in the 1990s?) and believe that their experience with cyber underwriting / claims / marketing / etc will help them generate profit from offering cyber insurance now in 2023.
I’m sure they will agree that cyber risks have evolved into a more complex beast. However, I don’t believe they are considering that the “complex beast” will continue to evolve to become unmanageable monsters with horrendously high (unprofitable) combined ratios in the months and years to come.
The voids will remain – and expand – and no imagination of cyber attack spaces with concomitant cyber attacks will yield financial success for (re)insurers or E&S insurers (or capital market players).