I’m not a doctor or any kind of healthcare provider. This blog post encompasses a jumble of assumptions, questions, and guesses. It palpably demonstrates that I am only a patient of the US healthcare system. But, I hope that I am making the right assumptions, questions, and guesses about hospitals (or the healthcare system overall) and cyber resilience. I’d like you to let me know with your comments to this blog post.
Trigger for this blog post
The trigger for this blog post is an article in Industrial Cyber News by Anna Ribeiro. The first paragraph stated that: “U.S. Senator Mark R. Warner calls upon the administration to swiftly develop and implement mandatory minimum cyber standards across the healthcare sector. The move follows ongoing concerns about cyber-attackers exploiting vulnerabilities in existing systems, and a major cybersecurity incident at Change Healthcare that affected billing and care authorization portals and led to prescription backlogs and missed revenue for providers.”
Source: https://industrialcyber.co/medical/senator-warner-pushes-for-immediate-action-on-mandatory-cybersecurity-standards-for-healthcare-sector/ , July 17, 2024 by Anna Ribeiro, Industrial Cyber News Editor
The Senator wants to “swiftly develop and implement mandatory minimum cyber standards across the healthcare sector”. It’s a worthwhile objective, putting aside the realities that nothing happens quickly in the US Congress, the time (months?) it will take Congress to hold the (many) information-gathering sessions with the “appropriate” healthcare and cybersecurity professionals (if they want to rationally accomplish the objective) and the fact that different Representatives and Senators will have different ideas regarding how to achieve the objective.
About my blog post’s title. I purposely avoided using the term ‘cybersecurity’. No organization (or enterprise) regardless of size or industry or governance structure or (_____________ you fill in the blank) can ever be cyber secure. It doesn’t matter whether the organization is – and remains – completely compliant with cyber security guidelines from their industry or the government.
Organizations, however, can and must strive to become cyber resilient. Hopefully, if they are cyber-attacked the organization’s cyber resilience solutions, processes, and protocols will place them in a stronger position of lessening the odds of being cyber-attacked again after they remediate their attacked situation.
But there are no guarantees. Even cyber resilient organizations – including the organizations that comply with every cyber security law, rule, and regulation that exists or will exist – can (and probably will) be cyber-attacked multiple times.
A Way Too Simple Consideration of Portals and Patients and Hospitals (Oh My!)
The healthcare sector encompasses a plethora of actors and (physical) entities including, but not limited to: healthcare professionals, pharmacists, hospitals, medical clinics, doctors’ offices (in private facilities, in hospitals, in clinics), pharmacies, drugstores, pharmaceutical companies, medical device manufacturers, rehabilitation facilities, health insurance companies, healthcare regulators, lawyers focused on healthcare practices, and (let us not forget) patients (and their caregivers and/or guardians).
I am positive that I have:
- missed many actors and physical entities participating in the healthcare sector;
- made mistakes in my healthcare sector / hospital statements below;
- made many assumptions that I need to clean up if I want to include a discussion like this in my book about the insurance industry and cyber risks that I’ve begun drafting.
I realize that before making cyber resilience comments, I should create healthcare sector maps of all types of players, facilities, ecosystems, value chains, medical devices and other medical equipment …and overlay data flows, distinguishing between different types of data as well as frequency of each data type being generated and the storage of each type of data as well as the inbound and outbound flow of each type of data … and access points by any person or physical entity within each component of the healthcare ecosystem to the web (as well as how, with which authority levels, and when the access happens).
I don’t plan on doing that for this blog post.
However, I will soldier on to discuss some much simpler aspects of patients, portals, and hospital settings.
The healthcare system: an ecosystem encompassing an extremely rich mixture of IT-enabled and OT-enabled organizations
The healthcare system is a living, breathing example of an ever-changing ecosystem encompassing a hybrid mix of IT-enabled and OT-enabled enterprises striving to deliver medical services to patients (some services delivered in real-time; other services delivered on a lag-time basis; some services delivered in one location for one patient; other services delivered in multiple locations for one patient).
The healthcare system is a true classic example of a hybrid mixture of an IT-enabled and OT-enabled service environment.
It is definitely a cyber predator target-rich attack space chock-a-block full, at a minimum, of:
- personal information (patient and medical professional);
- private medical / drug information (current and past patients);
- private financial information (patient);
- drug availability in hospital drug storage areas information;
- drug interaction / contra-indications information for each type of medicine prescribed for a patient or used in a procedure;
- intellectual property information (for each member company of the healthcare system);
- location information for each patient and for each organization in the healthcare system;
- procedure scheduling information for each patient and for each of the medical personnel involved in the procedure;
- medical professional scheduling information for patient visits / consults;
- hiring information for each organization in the healthcare system;
- medical organization competitive information for each organization in the healthcare ecosystem (e.g. acquisitions, mergers, layoffs, payroll, promotion, raises, physical addresses of each employee, email addresses of each employee, …).
Hospitals are a hybrid mixture of IT-enabled & OT-enabled capabilities
The hospital itself is a micro environment of IT-enabled capabilities (e.g., administrative functions; registering patients for procedures; checking patients out of the hospital; determining time and location availability of medical professionals in the hospital; maintaining patient portals) and OT-enabled capabilities (e.g., enabling and maintaining working order of every piece of medical equipment wherever the equipment is located in the hospital; ensuring the availability of the suite of pharmaceutical supplies, blood supplies, and medical equipment).
Each medical professional working in the hospital probably has a personal mobile device (whether smartphone or tablet or both) or is assigned a mobile device by the hospital. (We know that depending on the physical proximity of the personal mobile device to the hospital-assigned mobile device that cyber-hackers can extract hospital data from the personal device: air-gapping is not a solution for cyber protection.) Unless the medical professional keeps their personal mobile device powered off or puts it in a drawer of a desk in their medical office, it is probably a reasonable node on a predator’s cyber-attack target space.
Below I have inserted several visuals of components of a hospital (or healthcare system) to serve as examples of areas of possible cyber-attacks.
Quick High-Level View of Possible Hospital System Cyber-Attack Areas
Pharmacy Portal (for Patients and Patient’s Medical Providers)
CVS Caremark offers their customers a portal to: manage prescriptions, determine the status of their orders, determine costs and coverage information, and identify savings opportunities. A customer can access this portal on any of their smart mobile devices as well as on their computers (regardless of the browser they use).
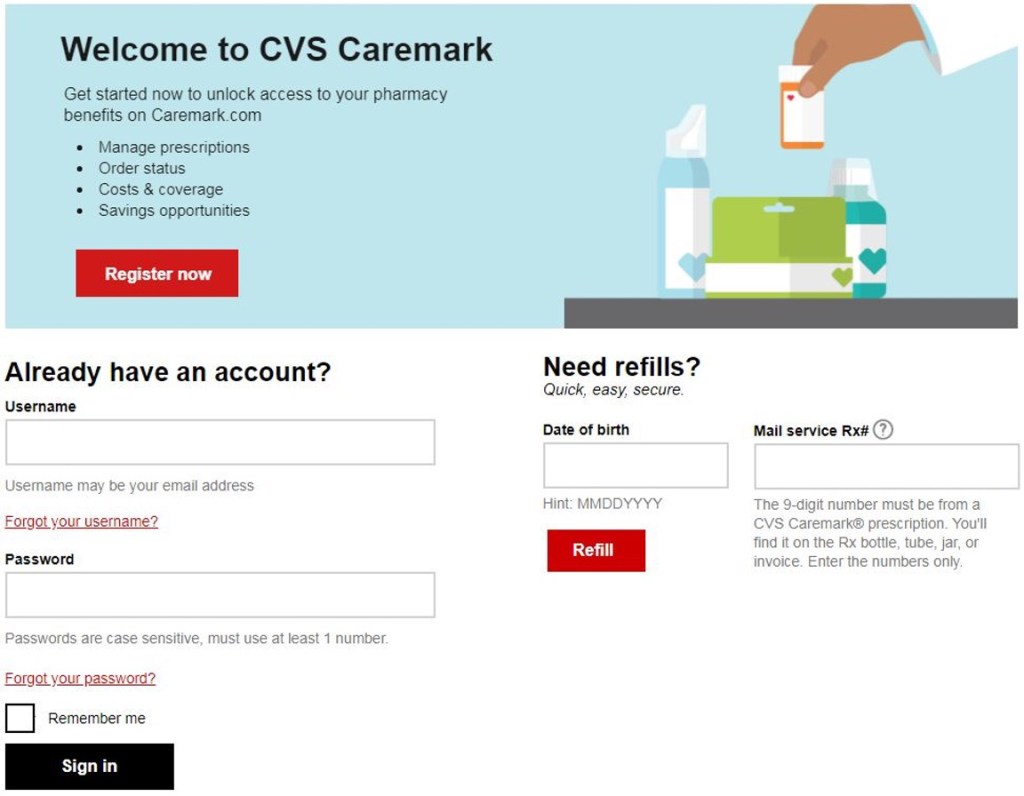
Source of visual: Bing.com
Hospital (or healthcare facility) Portal (for Patients and Patient’s Medical Providers)
Most hospitals offer a portal to their patients that is also accessible using mobile devices and computers. These portals and mobile device applications offer anytime, anywhere information for patients regarding their appointments, medical provider messages (to and from the patient), scheduled appointments, list of the patient’s medical providers with ability to email them or send them a message, current and historical lab results, and medical information. Some medical organizations also offer wellness and exercise information.
These hospital portals are deployed in the cloud, perhaps a public cloud solution from Microsoft, Amazon, or Google.

Source of visual: Bing.com
Physician’s (or physician’s aid or nurse’s or medical assistant’s or hospitalist’s) Office / Examination Room
A physician’s office / examination room provides both a ‘safe space’ for a patient examination and a probable ‘cyber-attack space’ directed at the laptop (or other computers in the room) if they are connected to the web, connected to the hospital’s systems (diagnostic, patient-facing, internal messaging, and/or hospital portal, …), or in close proximity to a patient’s (cyber-infected or otherwise compromised) mobile device, or in close proximity to the patient’s medical provider’s (cyber-infected or otherwise compromised) mobile device.
I also assume that one or more of the hospital systems are deployed in the cloud (possibly a public cloud such as one from Microsoft, Amazon, or Google).

Source of visual: Bing.com
Emergency Department Room
The Emergency Department rooms that are used to exam (and operate?) on patients have several medical devices which probably are connected to each other or to hospital systems (e.g., patient onboarding, diagnostic, in-hospital pharmaceutical, hospital supply and logistics management systems, and/or hospital-patient portal).
I assume at least one (if not more) of these systems are connected to the web. Any one of these systems may be deployed in a public cloud.

Source of visual: Bing.com
Operating Theatre Jungle of Equipment
I have a hunch that there is not any “unifying software solutions” that tie all of the operating theatre equipment together. I readily admit I could be wrong. Maybe some technology vendor offers “operating theatre software-as-a-solution”. Of course, that OTSaaS would still be a point-of-attack by cyber predators.
However, if any of the myriad pieces of equipment in the operating theatre are connected to the web – whether integrated with each other and/or integrated with other hospital systems – they represent a robust path for cyber havoc. Cyber-attacks in this arena could obviously cause death (or used to mislead the medical team to operate in the wrong area(s) of the patient laying on the table by altering the content or by changing the operating instructions of any of the web-connected equipment).

Source of visual: Bing.com
Doctor-Patient Examination (via Hologram)
This is obviously a “Princess Leia” situation that has become reality. The visual below represents a doctor ‘visiting’ a patient via hologram. My first thought was this channel was a perfect target for the use of deepfakes by cyber predators (to pretend to be doctors or other medical providers using the hologram) to get patient information.
I believe it would be a stretch to say this isn’t a cloud deployed solution. I assume that any of the major cloud providers could offer the infrastructure to enable holograms. I also assume that the hologram requires a robust wireless connection if a hard-wire line connection is not available.
I am curious how the ‘content’ of the conversation is digitally captured, and in which hospital systems (e.g., the hospital providing the medical professional with the hologram capabilities) the content is stored. I expect the content consists of voice / vocal files.

Source of visual: Bing.com
Initial Thoughts
Obviously, the visuals above represent only a select few of many points of interaction between:
- healthcare professionals within a healthcare system to communicate and collaborate on issues;
- healthcare professionals and patients (using a healthcare system’s portal or a hologram);
- healthcare professionals and the (pharmacy) portals used that capture pharmacy prescriptions for patients;
- patients and pharmacies (used by healthcare professionals for patients);
- hospital devices / equipment locations.
Healthcare systems are, as I mentioned at the beginning, a plethora of actors and (physical) entities including, but not limited to: healthcare professionals, pharmacists, hospitals, medical clinics, doctors’ offices (in private facilities, in hospitals, in clinics), pharmacies, drugstores, pharmaceutical companies, medical device manufacturers, rehabilitation facilities, health insurance companies, healthcare regulators, lawyers focused on healthcare practices, and patients.
The “actors” will all be using mobile devices (which are connected to the web) and a certain percent (large?) of the physical entities will be connected to the web. If even one physical entity is connected to the web but also connected to other physical entities (not connected to the web), the chain of these physical entities connected to each other represent a path for cyber-hackers.
I assume that discussing cyber risks, cyber predators, cyber-attacks, and cyber resilience with healthcare professionals is, in many ways, relatively straight-forward. Cyber attacks are essentially the spreading of viruses except in (sometimes mobile) digital, web-enabled (sometimes cloud-accessible) forms. Creating the ‘defenses’ to minimize the spread of these digital, web-enabled viruses is not foreign to healthcare professionals. One difference: medicine and other healthcare procedures can stop the spread of viruses but no amount of cyber security (or compliance regulations) can ever stop any organization, inclusive of any healthcare system, from being cyber-attacked.
Note: This cyber-focused WordPress blog post is potential material for my forthcoming book I’ve begun to draft about the insurance industry and cyber risks. Working title for my book: Insurance Commerce Ramifications in the Cyber Age. Target date to arrive at a final draft with my editor to turn it over to him at Wells Media is end of December 2025.