I drafted this blog post as a ‘thought piece’ to stir ideas about a modeler’s state of knowledge concerning 1) the existence and emergence of cyber attack spaces they have discovered (and not yet discovered), 2) the existence and emergence of cyber attacks they have discovered (and not yet discovered), and 3) characteristics of cyber risks that modelers either do include or might consider including in a cyber model (for predicting cyber losses or illegally-generated revenue from cyber attacks). I wanted to share my ‘beta’ version of my ideas about cyber risk “surfaces”, characteristics and model frameworks.
Cyber professionals talk about a cyber threat ‘surface’ but the term ‘surface’ is a problem for me. The term ‘surface’ triggers an image in my mind of a two-or-three dimension spatial illustration that lives on some geographic terrain. I think that the term encourages insurers and insureds to incorrectly perceive a cyber threat is just like the panoply of risks that they have faced for the previous hundreds of years.
The reality is that a cyber threat ‘surface’ is not a geographic surface area. A cyber threat is, or could be, a multi-dimensional (hyper-dimensional) spatial area (not necessarily with contiguous points) that has been, is, or could / will be attacked. It is not a straightforward geographic surface.
For me, a cyber threat is multi-dimensional not because the element of time is involved. (Time should always be an integral component of any cyber model.) But because a cyber attack could impact many parts of a corporation, or many physical artifacts (through its web connection), or many people or combinations of any of these.
Five examples of potential (or real?) cyber risks include:
- Attacking one company: all of its web-connected devices; every operating system the company uses to stay in business; the exfiltration of company proprietary information; and the exfiltration of every company client’s PII … simultaneously and without warning anywhere the company has facilities and/or business activities on the planet.
- Taking control of the web-connected capabilities of a vehicle to stop the vehicle while it is driving on a highway to cause multi-car crashes, several deaths, and multiple injuries.
- Combining Deep Fake (facial features, voice, images of damaged and repaired cars) with ChatGPT (create fake notice of loss forms, claim adjudication firms, insurer claim work flows, and claim settlement documentation) to perpetrate auto insurance fraud in multiple locations involving different automobiles against multiple automobile insurers.
- Exfiltration of biometric data (retinal scan, face, fingerprint, voice and speech patterns) from employees of one or more corporations for later use to commit identify fraud “at scale”.
- Exfiltration of city employee PII and financial data (e.g. pension information, social security benefits, banking information, credit card information) by penetration of the city’s human resource systems.
Portia said that “The quality of mercy is not strain’d” in William Shakespeare’s The Merchant of Venice (Act 4, Scene 1).
However, the quality (e.g. nature, including type of interconnections and interdependencies among and between digital artifacts and the digital content of physical artifacts [e.g. IoT]) and quantity of cyber risks – and concomitant cyber losses – have most assuredly changed over the many decades since the first computing device was hacked. And since the first cyber insurance policy was sold …
My question: How many months – or years – of cyber insurance combined ratios over 100% will it take for insurer’s patience to be strain’d to the breaking point to alter their decision about whether or how to participate in the cyber insurance market?
Characteristics of Cyber Risks
Any person modeling cyber losses from the point of view of the target (or modeling cyber illegally gained revenue from the point of view of the attacker) might incorporate any number of several cyber risk characteristics to shape their models.
Perhaps some of the following cyber risk characteristics are used in the models that (re)insurers, cyber protection service firms (e.g. firms that conduct cyber audits, provide real-time monitoring of cyber hacking, or create cyber loss models), or (government or industry) regulators focused on cyber security or cyber attackers use in their models :
- Topology of multi-dimensional cyber attack spatial area: Number and nature of attack areas
- Time of impact: Instantaneous (no warning from the cyber attackers)
- Behavior: Adaptive (as digital world continues to become an ever-more interdependent and interconnected business, commerce, and communication ecosystem)
- Scale: Multi-dimensional
- Reach: Any digital artifact and / or digital component of a physical artifact connected between and among each other and the web
- Visibility: None until unleashed (risk is unseen / unfelt as cyber-hack in target company’s systems)
- Repeat visitor: Second or later “visit” by same cyber attacker on same or different target (attacking the same corporation)
- Cost Model: Zero-cost to unleash; potential cost to “hire” / “use” cyber-hackers as a team
- Revenue Model: Sell (or lease) hack-as-a-service
- Patience: Lag-time from exfiltration of information (company proprietary information; PII of employers, clients, supply chain partners) to use of information (e.g. ransom, theft, sold to other illegal sources; cause company shutdown, …)
- Rogue State Protection: Yes (if protected by a rogue nation) or No
- Type: DDoS; Phishing; Ransomware; Business E-Mail Compromise; Deep Fake (voice with requisite speech patterns; face); Malware; Systemic Risk; Cyber warfare (e.g. asynchronous attack from a hacker protected by a Rogue Nation); LOTL; ? [one or more of these cyber attacks can be, are, or will be combined in one cyber attack]
- Genesis: Bot-driven; ChatGPT-driven; Person; Government
- ?
Obviously, the list is incomplete and I’m sure the “terms” I used for the various cyber risk characteristics could (should?) be worded in a better way. I’m open to any and all suggested additions of cyber risk characteristics and wording improvements.
Just a quick point about the Topology of the multi-dimensional cyber attack spatial area: in our ever-expanding, never-ending digital world of interconnections and interdependencies among and between web-enabled digital artifacts, digital content of physical artifacts, and physical artifacts, the complexity of the topology describing potential cyber attack spaces and cyber attacks will be, if they are not already, much greater than even being able to succeed at 5 dimensional chess. (See image from Bing below.)

A cyber modeling framework for two interdependent cyber forces: Prey and Predator
The cyber world, increasingly becoming the world of commerce, entertainment, and communications of society, is an every-expanding world of interconnections and interdependencies among and between digital artifacts, the digital content of physical artifacts, and physical artifacts. I submit that the nature of the cyber world, including the behaviors of current and future entities participating in it, will be similar to that of a digital ecosystem and as such, it will encompass some of the characteristics and principles of a natural ecosystem.
One of the principles of a natural ecosystem at play in a digital ecosystem is the predator / prey dynamic. This dynamic will shape – and continually reshape – the digital ecosystem, including the nature and number of current and future risks. The prey (e.g. targets of current and future cyber attacks) must identify and defend (e.g. secure) their assets (digital and digitized content of physical assets they own, lease, or use) from the predator’s attacks.
In practice, this means that the prey (e.g. every corporation, government entity, non-profit organization, healthcare facility, entertainment venue, grocery store, retail store, and customers, employees, and participants in the various ecosystems in which those organizations participate) must continually identify (e.g. discover existing and emerging) attacks as well as understand and defend how their existing and emerging attack spaces are or could be attacked.
There are two cyber truisms that I believe: 1) The cyber insurance market is nowhere near ‘mature’ (or stable), and 2) The spectrum of cyber risks in the digital ecosystem will get increasingly more complex with a mixture of short – and – long tail exposures.
A cyber modeling framework
I began thinking about a cyber modeling framework – for predators and prey – by basing it on “known” and “unknown” cyber risks. But it occurred to me that was too ‘macro’ to drive even high-level ideas about a model.
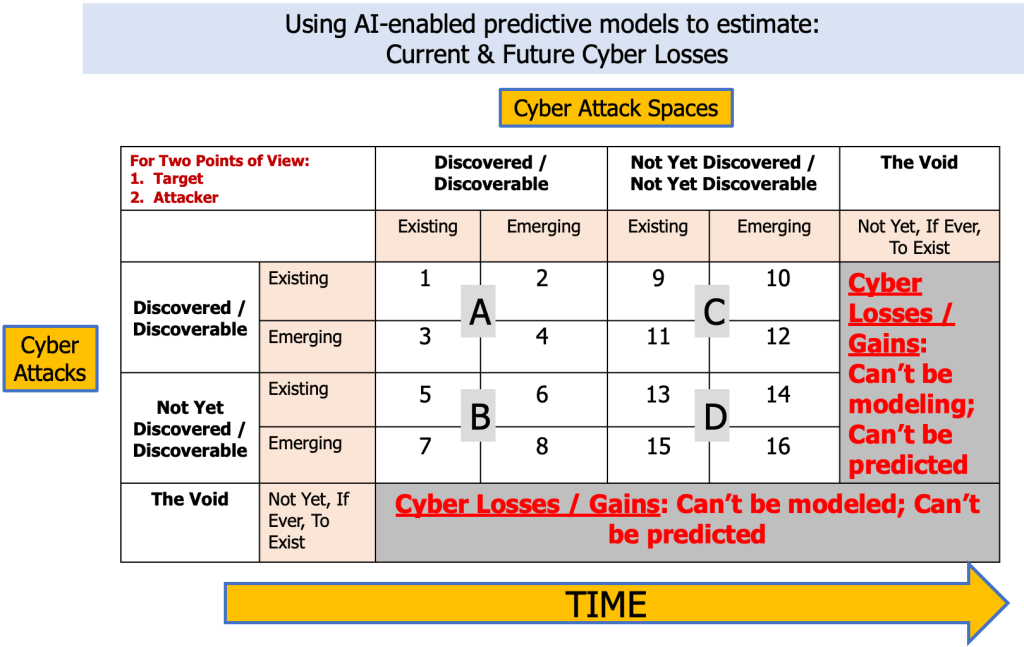
My next iteration is the framework (of two tables) below: one framework for a Prey mindset and one table for a Predator mindset. The main differences are in my placement of four zones (A, B, C, and D).
Using a Prey Mindset
Using a Predator Mindset

I suggest using the differently placed Zones if a modeler is using a Predator mindset. For me, this placement of Zones would enable Predators to continue to have an advantage over Prey by identifying cyber attacks and cyber attack spaces that Prey may not be able to identify as quickly as the Predators.
Brief discussion of the framework
I hypothesize that the Prey use their point-of-view and the Predator’s point-of-view to create cyber models (either to model and predict cyber losses or to model illegally-gained revenues).
Both cyber attack spaces and cyber attacks includes the notions of three categories: “Discovered / Discoverable”, “Not Yet Discovered / Not Yet Discoverable”, and “The Void”. For each of the first two categories, I introduce “Existing” and “Emerging” for cyber attack spaces and cyber attacks.
Obviously there are skills / experience / know-how elements at play for each firm’s modelers to identify discovered / discoverable cyber attack spaces and cyber attacks. Research, discussions with cyber professionals, and cyber conferences are three venues that could help move “discoverable” to “discovered” whether for cyber attack spaces or for cyber attacks.
I see the realm of “Not Yet Discovered / Not Yet Discoverable” as one that encompasses hypothetical instances whether of cyber attack spaces or of cyber attacks. As Not Yet Discovered / Not Yet Discoverable becomes “Discovered / Discoverable”, the firm’s modelers can document how, where, and when that happened … and potentially move the newly “Discovered / Discoverable” into the cyber model, if they believe appropriate.
There are several forces that could be considered singularly or in combination to support the hypotheses to identify potential “Not Yet Discovered / Not Yet Discoverable”: IT trends, Telco trends, Device trends (devices connected to the web), IoT trends, Communication trends, Commerce trends, and Entertainment trends.
There is also a time element at play within the rows and columns of the framework: what is “emerging” depends on whether a firm’s modelers actually know about the existence of a cyber risk and when that cyber risk appeared as a actual hack. Moreover, modelers might feel that some “Existing” aspects (whether cyber attack spaces or cyber attacks) could be left out of models, for whatever reasons.
I intend “The Void” to be an area where no data, no model, no predictions of cyber losses (or for the predators, no illegally gained revenue) exist because The Void is a ‘nothingness’ and no model can “see into it or around corners”. For me, what comes to mind about The Void is “The night is dark and full of terrors” as the red priestess Melisandre said in Game of Thrones. I believe that emergent cyber attack spaces and/or cyber attacks will be born in The Void for firm’s modelers to discover and consider whether to include in their models.
Time plays a critical role for the entire framework, inclusive of The Void and what cyber attack spaces and cyber attacks may or may not emerge from it. Cyber attack spaces and cyber attacks are ever-changeable and ever-changing: the intersection of the two generates, or will generate, cyber risks that are novel and haven’t previously been experienced. Any firm (modeler, (re)insurer, regulator) that stakes their future on the “well, we’ve seen this before and can manage it” is holding a financially dangerous philosophy (e.g. financially dangerous to the combined ratios of insurers).
The Zones could be used for selecting priorities of groups of models. For the Prey, I suggest they use the Zones shown in the “Predator Mindset” framework.
Regardless of the Predator or Prey mindset, I assume each cell of the zones will be full of multiple sets of models. In addition, I assume that models of aggregate cyber risks could be the sum of the results of models from two or more cells. (Excluding The Void, of course.)
Over to you
I’m interested in your comments. What did you find useful or, at least, interesting about this post?