I believe that our world – inclusive of the surface, below in our oceans and lakes and rivers, and above it in the air and in space – is becoming cyber-formed.
The cyber-forming is driven by the almost uncountable vast number of multi-dimensional cyber attack spaces that are continually wrapping themselves around and through everything, every process, and everybody and everything connected to the web.
Every moment a digital artifact is connected to the web, it is becoming simultaneously part of the fabric and a new entry point for hackers to the never-ending, always-expanding multi-dimensional cyber attack space;
Every moment a physical artifact with digital content and/or telecommunications capabilities is connected to the web, it is becoming simultaneously part of the fabric and an entry point for hackers to the never-ending, always-expanding multi-dimensional cyber attack space;
Every moment a Non-Human Entity is connected to the web, it is becoming simultaneously part of the fabric and a new entry point for hackers to the never-ending, always-expanding multi-dimensional cyber attack space;
Every moment a sentient being (with some IP-sensor attached to it or embedded in it) is connected to the web, it is becoming simultaneously part of the fabric and a new entry point for hackers to the never-ending, always-expanding multi-dimensional cyber attack space.
Thinking of the cyber attack space as a cyber attack surface is limiting. A ‘surface’ is, at best, three-dimensional. I believe the cyber attack topography is multi-dimensional (and multi-directional).
Visually, I think it’s more like ‘ribbons’ of different colors, sizes, and shapes that perpetually alter (mutate?) their appearance and strengthen their capabilities to both: a) create, enable, and support objectives society wants to achieve quickly, and b) provide entry points for cyber hackers to disrupt, corrupt, or destruct either society’s paths to achieving their objectives or the objectives themselves or both.
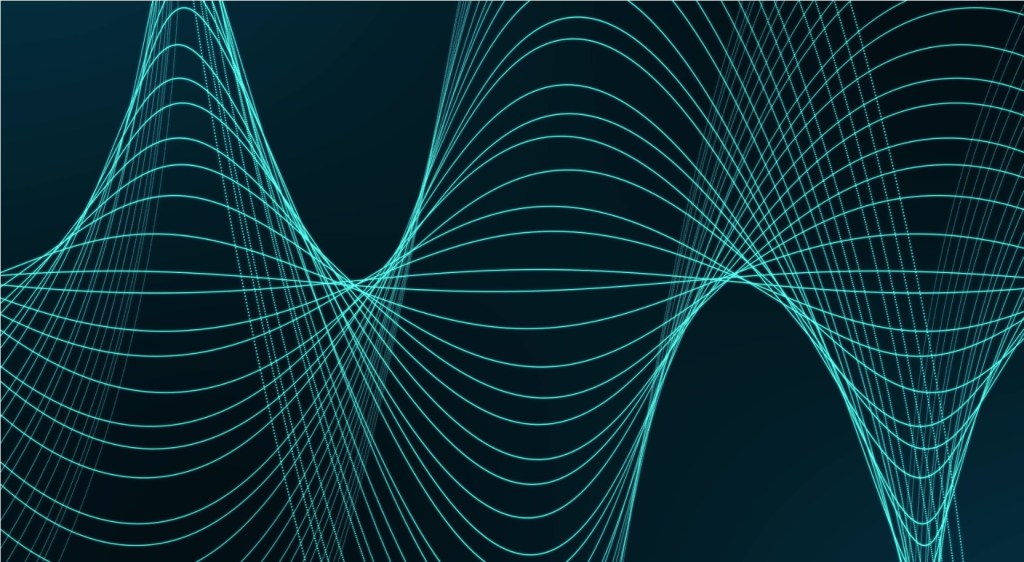
Image of Particle Ribbons found on Bing.com
I believe that most of us (humans) can’t see that the cyber-forming is happening. Too many of us believe in “point solutions” (e.g. The discussion goes something like ‘Of course that’s not a systemic cyber risk because only that one company or that one functional area of that company was cyber-attacked’).
The reality is that a cyber-attack that emerges at any part of the cyber attack Nth dimensional topography cascades though other elements of the topographical multi-dimensional, multi-directional space – or to state it another way, other parts of the always-in-motion ribbons are impacted (and continue in-motion).
That’s why I don’t believe that any person or any firm can model future cyber losses or realistically state that they can stop or slow down cyber attacks. The ribbons continue to mutate as they expand in multiple dimensions and multiple directions simultaneously.
I read articles that essentially say that “We’ve stopped this or that group of cyber attackers.” That’s nice. But to me, I hear: “hey, we’ve brushed back the ocean on this part of the beach that was being impacted by the waves”.
The ribbons don’t care. They continue to grow, to expand, to mutate because they are continually fed by new or changed artifacts connected to the web.
Cyber-forming, and its always-evolving cyber attack topography and associated plethora of cyber risks, continues unabated without regard to government cyber regulations or industry cyber regulations or to the compliance of any enterprise to either or both of those types of cyber regulations.
Really good food for thought, Barry. Happy New Year!
LikeLike
Thanks for your comments.
Better than me saying that cybersecurity firms that tell clients that they can stop or slow down cyber attacks playing the “long con” (and that their business model is based on no-one able to prove a negative) … but they are. I agree cybersecurity firms are required to help corporations become cyber resilient but when they say that can stop or slow down cyber attacks, I react.
LikeLike
Will it be Minority Report or back to the dark ages – or do you see a solution in between?
LikeLike
Great question: I need to think about it for a while. I probably should take a stab at answering it in my book. (Perhaps a scenario planning format to answer it?)
LikeLike