In this post I discuss my:
- Description of cyber attack spaces;
- Thought process to get to the metric: ‘Density of Interdependence’ of cyber attack spaces;
- List of my working hypotheses as some bit of context;
- Choice of a visual to use the ‘Density of Interdependence’ metric;
- Marked up visual to support thinking about the metric;
- Possibilities about the metric itself;
- Request for your comments / ideas about the metric.
Describing Cyber Attack Spaces
Cyber Attack Spaces are neither stable nor are they static. They are a ceaselessly growing multitude without end.
What are cyber attack spaces?
Cyber attack spaces are created, and continue to expand in multiple dimensions and multiple directions, by the continuing growth of interdependencies and interconnections among and between digital artifacts, physical artifacts with digital content (and/or telco capabilities), and physical artifacts.
Cyber attack spaces grow and expand in multiple dimensions and multiple directions each instant (not an exclusive list):
- an altered or new digital artifact is connected to the web;
- a new physical artifact with embedded content is connected to the web;
- a new physical artifact with Telco capabilities embedded in it or on it is connected to the web;
- a person or animal or insect with an IP sensor is embedded in it or on it is connected to the web;
- one or more digital artifacts connected to the web and/or one or more physical artifacts with digital content (or Telco capabilities) connected to the web are connected to each other or made interdependent with each other;
- one or more digital artifacts connected to the web get new content or are replaced with a new digital artifact connected to the web and/or one or more physical artifacts with digital content (or Telco capabilities) connected to the web get new digital content or altered digital content (or new Telco capabilities or altered Telco capabilities) are connected to each other or made interdependent with each other;
- a digital piece of content embedded in a physical artifact already connected to the web is altered or replaced with new content;
- a physical artifact with telco capabilities embedded in it (or on it) gets altered or new telco capabilities embedded in it (or on it);
- a new physical artifact thought to be air-gapped but actually isn’t air-gapped is brought near an altered or new digital artifact connected to the web;
- a new physical artifact thought to be air-gapped but actually isn’t air-gapped is brought near an altered or new physical artifact with digital content already connected to the web;
- a new physical artifact thought to be air-gapped but actually isn’t air-gapped is brought near an altered or new physical artifact with telco capabilities already connected to the web.
The existence of ever-growing, ever-changing cyber attack spaces are a reality for humans similar to the sun rising in the East and setting in the West.
Cyber Attack Space Metric: Density of Interdependence
With my description of cyber attack spaces above, let’s turn to the potential metric I call “Density of Interdependence”.
My intent for the metric is to capture the depth of cyber attacks at any point(s) or location(s) on (or along) one or more cyber attack spaces that comprise a multi-dimensional cyber attack space. I have no idea how the metric could be calculated. Moreover, I’m not sure the metric could ever be calculated.
My thought process to get to the metric
When I began thinking of the metric, I flashed on a “density of risk” metric. I occasionally referred to this metric when I wrote insurance industry analyst reports discussing the total risks (within life, within health, within annuity, within personal insurance P&C lines of business, and within commercial insurance P&C lines of business) that were or could be brought into play for any one insurer or for all insurers when one or more all-encompassing loss events occurred (e.g., 9/11; severe weather events; global pandemics, …).
I included in my thought-process that I believe that almost (all?) cyber attacks are essentially systemic cyber attacks. You know, the reality that “no man is an island” (thank you, John Donne).
A visual to support the use of the metric
At that point in my thinking about the metric, I wondered what type of visualization I could use to help me and people reading this WordPress blog post to understand what I meant by the “density of interdependence” metric.
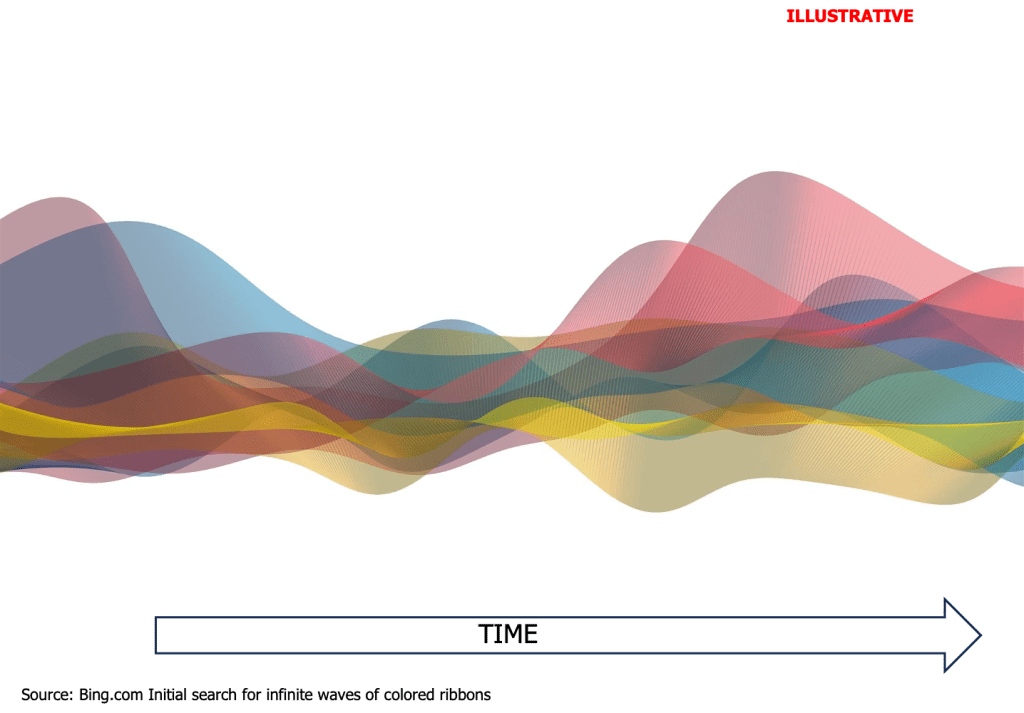
My answer: a visual of a multiplicity of colored ribbons cascading over and under each other through infinity.
A multiplicity? Yes. I believe that at each instant in time there are a multiplicity of cyber attack spaces cascading through cyberspace. For me, cyberspace is the fusion of four technologies (and their associated applications): digitization, mobility, Internet (although I tend to think about and write “web” – the GUI of the Internet), and cloud.
People, companies, towns / cities / States, Federal Government, hospitals, educational facilities, and entertainment venues are not potential victims of cyber risks from one cyber attack space. All of these entities are potential victims of cyber risks emerging on an always-growing number and always-changing nature of cyber attack spaces which unfold through infinity. (There is not any stability, any maturity, any ‘we got it handled’ regarding cyber attack spaces and yet-to-emerge cyber attacks.)
I found the visual below on Bing.com that I thought would do nicely for a discussion of this metric of density:
Describing the Cyber Attack Space ‘Density of Interdependence’ metric
To repeat the set of points I mentioned above because of their critical importance – cyber attack spaces are not static. They are dynamic: they are continually growing, their nature is continually changing, and they continually expanding in multiple dimensions and multiple directions. They are neither becoming “stable” nor are they becoming “mature”.
The metric I propose is not a ‘magic bullet’ to corral where the cyber attack spaces can grow, expand, or change their evolving nature. I see the ‘Density of Interdependence’ metric could (would?) be of assistance determining the depth, breath, and insured monetary volume of potential losses of cyber attacks that emerge at various points on one cyber attack space or somewhere on a spectrum of two or more cyber attack spaces.
By ‘spectrum’, I do not mean only a horizontal consideration of a specific location of one cyber attack space but a holistic perspective inclusive of all degrees of the collection of cyber attack spaces flowing through the varied dimensions and directions that attack one or more companies (or industries or other entities) simultaneously.
Possibly the metric – in conjunction with other metrics [no, I don’t know which other metrics] could be used in a hedging model, guide (re)insurers to tighten cyber insurance policy terms, caution insurers about what markets to leave (e.g. MSPs, hospitals), or provide guidance to insurers to stop selling cyber insurance entirely. I realize that I’m pinning way too much hope on the beneficial aspects of a metric that I don’t believe can be calculated.
Working Hypotheses as context for thinking about the metric
Here are my working hypotheses as additional context for thinking about the metric;
- Every company regardless of industry or size participates in at least one ecosystem;
- An ecosystem could consist of sales channels, suppliers, storage / warehousing, distribution channels, regulators, clients, prospective clients, external law firms, external auditors, healthcare inclusive of rehabilitation professionals, property remediation professionals, banks / financial organizations (that commercial property owners use to fund restoration of destroyed / damaged property) …
- Any company could be cyber-attacked more than one time;
- Any company participating in the cyber-targeted and cyber-attacked initially targeted company ecosystem could be cyber-attacked more than one time;
- Complying with government cyber regulations will not stop any company from being cyber-attacked multiple times;
- Complying with industry cyber rules / guidelines / advice will not stop any company from being cyber-attacked multiple times;
- Purchasing the services of cyber advisory firms / cyber protection / cyber modeling firms will not stop any company from being cyber-attacked multiple times;
- Following the advice of legal counsel (whether in-house or external law firm) will not stop any company from being cyber-attacked multiple time;
- Purchasing cyber insurance will not stop any company from being cyber-attacked multiple times;
- Participating in a Captive focused on cyber risks will not stop any company from being cyber-attacked multiple times;
- Participating in an Insurance Linked Security (ILS) cyber cat bond will not stop any company from being cyber-attacked multiple times.
Let’s get into the crux of the metric with the more detailed visual below.
A visual to support thinking about the metric
Diving into the infinite waves of cyber attack spaces (see visual below):

- the ‘Density of Interdependence’ metric captures the cyber losses from all of the cyber-attacks that could occur – or do occur – on one or more cyber attack waves. Any one entity could be cyber-attacked from cyber risks emerging on one or more cyber attack spaces. (e.g., The occurrence of a cyber attack at an instance of time on a company never precludes the same, similar, or other future cyber-attacks emerging on the same cyber attack space or other cyber attack spaces which the entity is exposed to at the same or any future instance of time.)
- each wave represents one cyber attack space unfolding through time into infinity without end;
- the height of each single wave represents the number of entities (e.g., employees, clients, processes, facilities, information, intellectual capital, money) within an company (or any other type of organization) that could be cyber-attacked at any point on or location of the wave;
- the distance from the top of the top-most wave to the bottom of the lowest wave (in the visual) at a slice of time represents the total number of companies and associated entities that could be cyber-attacked at any point on or locations of the combination of waves;
- if a wave moves through time beyond one location (the visual should include waves that exist only a single moment of time) means cyber-attacks can be perpetuated on one or more members (employees, clients, prospective clients, facilities, processes, information, intellectual capital, money) of the target company’s ecosystem members at future instances of time;
- the distance between the height of the same colored wave to the height of the next, similarly colored wave as it moves through time represents the frequency of possible cyber attack(s) occurring on the same cyber attack space;
- the scale of time for any one cyber attack occurring on the same cyber attack space could range from nanoseconds (or quicker) to years (before the cyber-hackers decide to do something with whatever they exfiltrated during their cyber-attack of the primary target or the primary target’s ecosystem members);
- blended colors of fused cyber attack spaces represent a convergence of two or more cyber attack spaces occurring at a point in time.
I know I have missed other possibilities involving time, numbers (and types) of entities that the cyber attack spaces could encompass, and specifically more discussion of frequency and severity of cyber attacks that could emerge from each of the cyber attack spaces or all of the cyber attack spaces which exist at an instance of time.
Taking license
Beyond what I missed, I took ‘license’ by using the word ‘company’ where I wanted to include any person, group of people, or for-profit or not-for-profit organizations that use 1) digital artifacts connected to the web, 2) physical artifacts with embedded digital artifacts and/or Telco capabilities connected to the web, or 3) physical artifacts supposedly air-gapped but not air-gapped next to either digital artifacts connected to the web or physical artifacts with embedded digital content / Telco capabilities connected to the web – or some combination of each of these three. Note also that my use of ‘physical artifacts’ includes humans, animals, or insects any of which could have (and do) IP-enabled sensors embedded in them or attached to them.
Possibilities about the metric itself
We’re in the guts of it, now. What are some of the possibilities of the metric?
I’m going to leave this to the modelers, statisticians, data scientists, and other quants out there.
Just a few thoughts about the metric, though. I see:
- The metric has having a lower and upper limit – maybe between 1 and 10 where the upper limit means extremely high density of interdependence of cyber attack spaces.
- The number and diverse nature of cyber attack spaces flowing through more than one target with a concomitant set of numbers of cyber attacks and diverse types of cyber attacks against more than one target emerging from the same (or limited spread of) location(s) contributing to a higher upper limit.
- That a slice of cyber attack spaces and a higher number and diversity of cyber attacks would contribute to a higher upper limit. Going back to the marked-up visual, I see the metric being higher in the “B” region than in the “A” region. (I bet you thought I forgot about those two regions with letters ?)
What do you think? How would you describe or calculate this ‘density of interdependency’ metric?
Note: I welcome any comments, suggestions, ideas about the Density of Interdependence Metric. I also welcome any comment that directly states that “I’m crazy” regarding the metric.